RSA Authentication Manager
Identities ❌ | Accounts ✔️ | Groups ✔️ | App Roles ❌ | Entitlements ✔️ |
Admin Roles in RSA Authentication Manager define permissions and responsibilities for system administrators, allowing them to manage user authentication and security settings.
Tokens in RSA Authentication Manager are physical or software-based devices that generate one-time passcodes. Users enter these passcodes during authentication, enhancing security.
Risk-Based Authentication in RSA Authentication Manager evaluates various factors such as user location, device, and behavior patterns to assess the risk level. Based on this assessment, it adapts the authentication process, adding or reducing security measures accordingly to mitigate potential risks.
- The PostgreSQL JDBC driver has been uploaded via the admin console.
- The RSA Authentication Manager certificate
RSAAMTrustedRootSSLCA.crthas been imported via admin console. - To enable RSA Identity G&L to connect to PostgreSQL database, a read only user has to be created using the
rsautil manage-readonly-dbuserstool. Refer to SQL Access to the RSA Authentication Manager Database section in the RSA Authentication Manager 8.x Developer's Guide for detailed information.
Application
The first step in collecting accounts, tokens information from RSA Authentication Manager is to create a placeholder application to store this information in RSA Identity G&L.
Steps
- Login to RSA G&L console as System Administrator.
- Navigate to Resources > Application.
- Click on Create Application and select Other Application.
- Enter the details as shown below. If you intend to collect the account status and/or the locked status of the account configure the highlighted options.
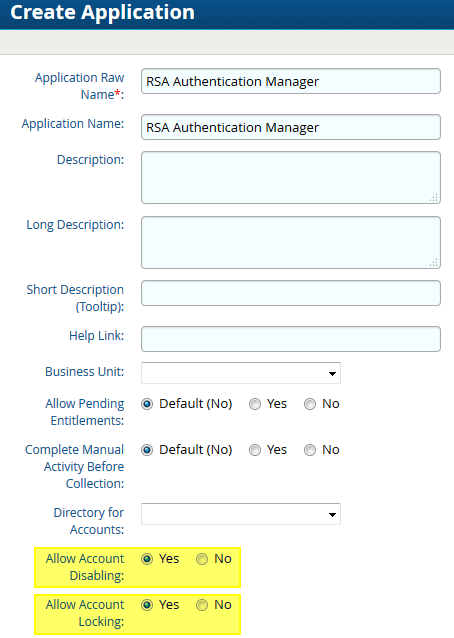
- Click Finish.
Account Collector
This section explains the process for configuring a account collector for the RSA Authentication Manager application. We will use the PostgreSQL database collector for this purpose.
Steps
- Login to RSA G&L console as System Administrator.
- Navigate to Resources > Applications.
- Click on RSA Authentication Manager.
- Navigate to Collectors tab and click on Create Account Collector. Enter the details as shown below.
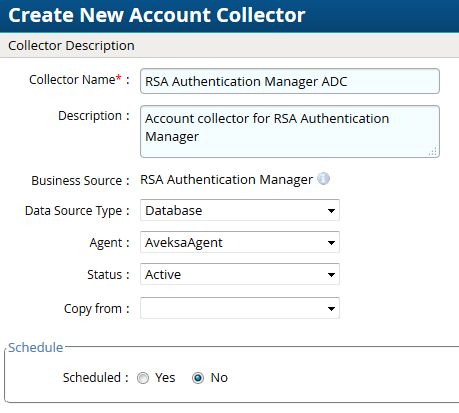
- Click Next and enter the PostgreSQL database connection details. Use the Test Connection to make sure the connection details are accurate.
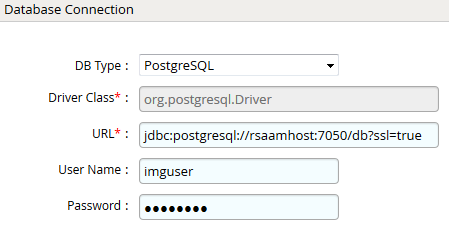
- Click Next. Select the appropriate data that you intend to collect. For the purpose of illustration we will collect accounts, groups and user to account mapping from RSA Authentication Manager.
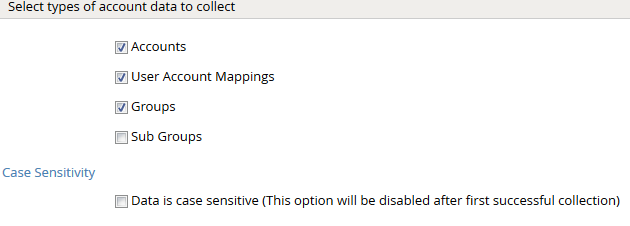
- Click Next. On the Account Data page, enter the following query to collect account information.
SELECT DISTINCT principalData.loginuid AS account
,login.login_date AS login_date
,CONCAT (principal.first_name, ' ', principal.last_name) AS full_name
--1 = enabled, 2 = disabled
,CASE
WHEN principalData.lockout_flag = '1' THEN '1'
ELSE '0'
END AS account_locked
,securityDomain.NAME AS securityDomain_domain
,CASE
WHEN principalData.security_ques_answers IS NULL THEN '0'
ELSE '1'
END AS securityDomain_questions,
--1 = user is enabled, 0 = user is disabled
CASE
WHEN principalData.enable_flag = '1' THEN '0'
ELSE '1'
END AS account_status
--1 = user has administrative roles assigned
--0 = user does not have any administrative roles assigned
,principalData.administrator_flag AS privileged
--Basic user settings
FROM IMS_PRINCIPAL principal
--Detailed information about the user
FULL JOIN IMS_PRINCIPAL_DATA principalData
ON principal.loginuid = principalData.loginuid
--Information about the security domain
JOIN IMS_SECURITY_DOMAIN securityDomain
ON principalData.owner_id = securityDomain.id
--Last logon date and time of the user
JOIN IMS_PRINCIPAL_LOGIN_DATE login
ON principalData.id = login.principal_id
The following are the important attributes
8. Click Next. On the User Account Mappings Data configuration page enter the following query to map the RSA Authentication Manager account to user identity.
SELECT DISTINCT
loginuid,loginuid AS account
FROM
rsa_rep.IMS_PRINCIPAL_DATA
The following are the important attributes
9. Click Next. In the Group Data configuration section enter the following query to collect groups from RSA Authentication Manager.
SELECT DISTINCT
(name) AS "group"
,description
FROM
rsa_rep.IMS_GROUP_DATA
-- Optional Filter
WHERE
identity_src_id = 'The Identity Source ID'
The following are the important attributes
10. In the Account Membership Data configuration section enter the following query to collect groups membership information from RSA Authentication Manager.
SELECT
accounts.loginuid AS account
,GROUPS.name AS "group"
FROM rsa_rep.IMS_PRINCIPAL_DATA accounts
JOIN rsa_rep.IMS_PRINCIPAL_GROUP groupMembership
ON accounts.id = groupMembership.principal_id
JOIN rsa_rep.IMS_GROUP_DATA GROUPS
ON groupMembership.group_id = GROUPS.id
-- Optional Filter
WHERE
GROUPS.identity_src_id = 'The Identity Source Identitfier'
- Click Next. In the User Resolution Rules, map the user to account
| Target Collector | User Attribute |
|---|---|
| Users | User Id |
- Click Next. In the Member Account Resolution Rules, map the account collector.
| Target Collector | Account Attribute |
|---|---|
| RSA Authentication Manager ADC | Account Name |
- Click Finish. Use the Test function to make sure the configurations are accurate.
Entitlement Collector : Admin Roles
This section explains the process for configuring a entitlement collector to collect admin roles from RSA Authentication Manager application. We will use the PostgreSQL database collector for this purpose.
Steps
- Login to RSA G&L console as AveksaAdmin.
- Navigate to Resources > Applications.
- Click on RSA Authentication Manager.
- Navigate to Collectors tab and click on Create Entitlement Collector. Enter the details as shown below.
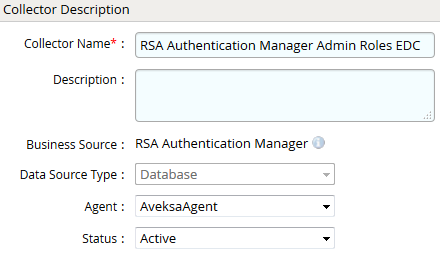
- Click Next and enter the database connection details as shown in Step 5 of Account Collector.
- Click Next. Select the data types that the collector will be collecting from RSA Authentication Manager.
- Click Next. On the General Column Names, map the attribute names.
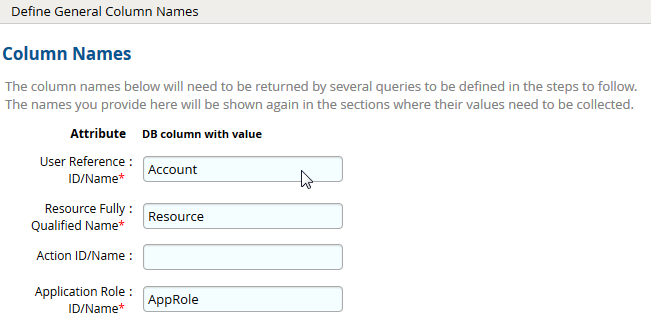
- Click Next. Under Application Role Data section, use the following query to collect admin roles from RSA Authentication Manager.
SELECT
name AS AppRole
,description
FROM
IMS_ADMIN_ROLE
The following are the important attributes
9. Click Next. On the Account Data section, enter the query below to collect mappings for account to admin roles.
SELECT
users.loginuid AS Account
,ROLES.name AS AppRole
FROM IMS_PRINCIPAL_DATA users
JOIN IMS_PRINCIPAL_ADMIN_ROLE admins
ON users.id = admins.principal_id
JOIN IMS_ADMIN_ROLE ROLES
ON admins.admin_role_id = ROLES.id
- Click Next. In the User Evaluation, map the account to the ADC.
| Associated account collector | Account value evaluates to |
|---|---|
| RSA Authentication Manager ADC | Account Name |
- Click Next and then click Finish. Use the Test function to make sure the configurations are accurate.
Entitlement Collector : Tokens
This section explains the process for configuring a entitlement collector to collect tokens as account entitlements from RSA Authentication Manager application. We will use the PostgreSQL database collector for this purpose.
Steps
- Login to RSA G&L console as AveksaAdmin.
- Navigate to Resources > Applications.
- Click on RSA Authentication Manager.
- Navigate to Collectors tab and click on Create Entitlement Collector. Enter the details as shown below.
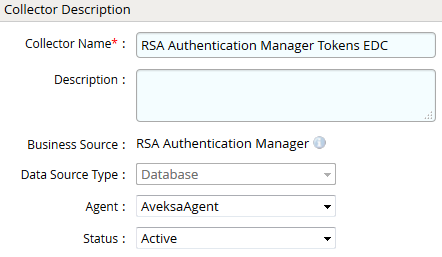
- Click Next and enter the database connection details as shown in Step 5 of Account Collector.
- Click Next. Select the data types that the collector will be collecting from RSA Authentication Manager.
- Click Next. On the General Column Names, map the attribute names.
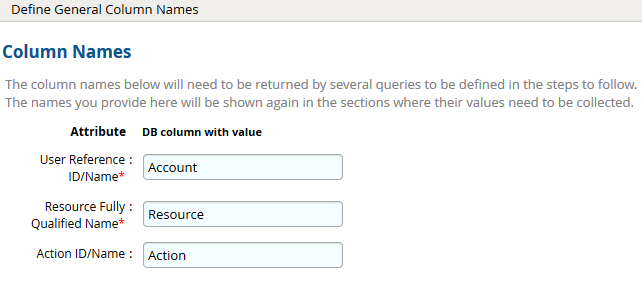
- Click Next.
- Click Next on the Resource Data page.
- Click Next. Under Resource Entitlement Data section, use the following query to collect tokens information from RSA Authentication Manager.
SELECT
tokens.serial_number AS RESOURCE
,CASE
WHEN tokens.token_type = '0' THEN 'Std Card'
WHEN tokens.token_type = '1' THEN 'PIN Pad'
WHEN tokens.token_type = '2' THEN 'SID 700'
WHEN tokens.token_type = '4' THEN 'Soft Token'
WHEN tokens.token_type = '9' THEN 'SID 800'
WHEN tokens.token_type = '10' THEN 'Flex Card'
END AS Action
,tokens.token_shutdown_date AS Expiration
,tokenDetails.last_login_date AS lastlogin,
CASE
WHEN tokens.is_enabled = 'true' OR tokens.is_enabled = 't' THEN 'true'
ELSE 'false'
END as tokenEnabled
FROM AM_TOKEN tokens
,AM_TOKEN_OOB tokenDetails
WHERE tokens.id = tokenDetails.am_token_id��
- Click Next. On the Account Data section, enter the query below to collect mappings for account to tokens.
SELECT users.loginuid AS Account
,serial_number AS RESOURCE
,CASE
WHEN token_type = '0' THEN 'Std Card'
WHEN token_type = '1' THEN 'PIN Pad'
WHEN token_type = '2' THEN 'SID 700'
WHEN token_type = '4' THEN device.family_key
WHEN token_type = '9' THEN 'SID 800'
WHEN token_type = '10' THEN 'Flex Card'
END AS Action
FROM IMS_PRINCIPAL_DATA users
JOIN AM_TOKEN tokens
ON users.id = tokens.principal_id
LEFT JOIN AM_SW_TOKEN_DEVICE_TYPES device
ON tokens.sw_token_device_type_id = device.id
- Click Next. In the Account Evaluation, map the account to the ADC.
| Associated account collector | Account value evaluates to |
|---|---|
| RSA Authentication Manager ADC | Account Name |
- Click Next and then click Finish. Use the Test function to make sure the configurations are accurate.
Entitlement Collector : Risk Based Authentication
This section explains the process for configuring a entitlement collector to collect information regarding Risk Based Authentication (RBA) being enabled for an account from RSA Authentication Manager application. We will use the PostgreSQL database collector for this purpose.
Steps
- Login to RSA G&L console as AveksaAdmin.
- Navigate to Resources > Applications.
- Click on RSA Authentication Manager.
- Navigate to Collectors tab and click on Create Entitlement Collector. Enter the details as shown below.
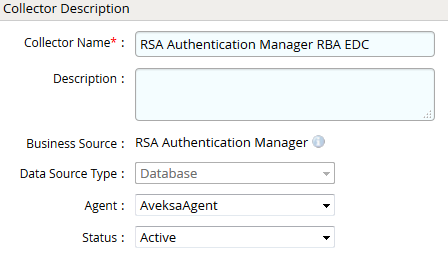
- Click Next and enter the database connection details as shown in Step 5 of Account Collector.
- Click Next. Select the data types that the collector will be collecting from RSA Authentication Manager.
- Click Next. On the General Column Names, map the attribute names.
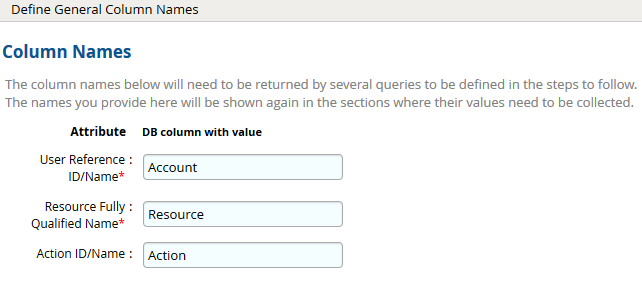
- Click Next.
- Click Next on the Resource Data page.
- Click Next. On the Account Data section, enter the query below to collect mappings for account to tokens.
SELECT loginuid AS Account
,'RBA' AS RESOURCE
,CASE
WHEN SUBSTR (authenticator_bit_flags, 7, 1) = '1' THEN 'Yes'
ELSE 'No'
END AS Action
FROM
IMS_PRINCIPAL_DATA
- Click Next. In the Account Evaluation, map the account to the ADC.
| Associated account collector | Account value evaluates to |
|---|---|
| RSA Authentication Manager ADC | Account Name |
- Click Next and then click Finish. Use the Test function to make sure the configurations are accurate.
COL027
